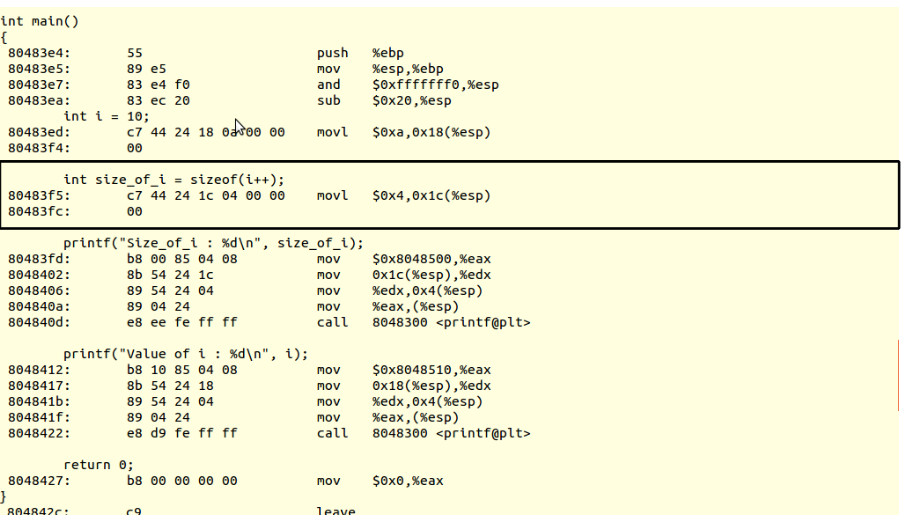
Void Pointers :
Definition
Void pointers are the
pointer variables which has no specific data type. These are also
called as Generic pointers because it can point to any data type. In
General, the compiler has no idea what type of object a void Pointer
really points to.
Void Pointers :
Declaration
A void pointer is declared like a
normal pointer, using the keyword “void” as the pointer’s type
as shown below,
Referencing &
De-referencing the void pointers
In order to explain, how void
pointers can be referenced & De-reference, let we take a small
sample code as shown below in
Fig
1,
Fig 1: Referencing & De-referencing
of the void pointers
From
the above Fig 1, it is clear that while referencing the void * no
need to typecast, only when De-referencing the void *, it need to be type-casted otherwise the gcc compiler will give warning along with
error note as shown below in Fig 2,
Fig 2: Result obtained while
de-referencing the void pointer without typecasting.
Fig
3: Output after typecasting the void pointer while dereferencing.
Why void pointers are
useful ?
One
main advantage of using the void pointers is that it can be
're-usable'.
Because
of this feature of the void pointers 'space' & 'time'
complexities can be reduced to some extent which is very critical in
Embedded System designing.
They are
very useful when you want a same
pointer to point to data of different types at different times.
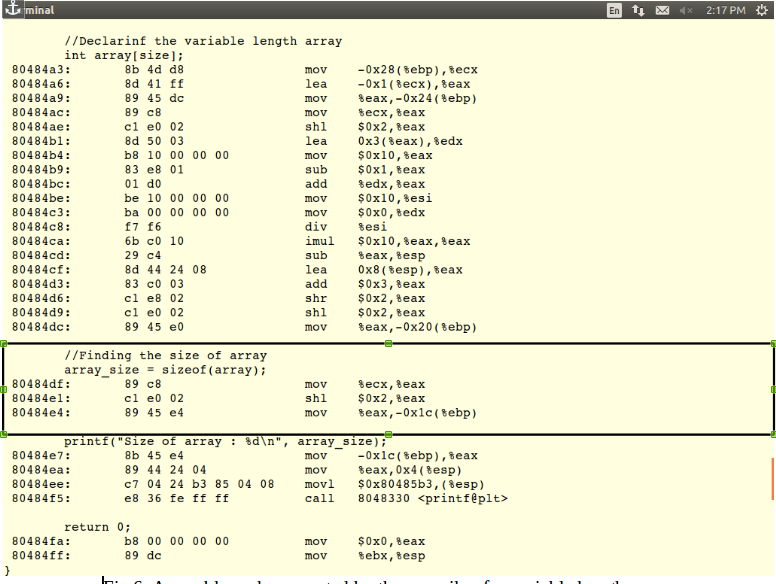
Let us consider a small simple
code snippet, to show how void pointers can be re-usable which
reduces the space complexity
in the
example as shown in the Fig 4
given below,
Fig 4: Void pointer reusability.
Fig 5: Output of the code shown in Fig
4.
For more clarity let us understand the
above code through pictorial representation.
Line No.14 : The vptr is pointing
to the address of the integer variable 'i', as shown below in Fig 6.1
Line No.18
: The vptr is pointing to the address of the character
variable 'c',
as shown below in Fig 6.2
Line
No.22
: The vptr is pointing to the address of the float
variable 'f',
as shown below in Fig 6.3
Line No.26
: The vptr is pointing to the address of the double
variable 'd',
as shown below in Fig 6.4
Note : xxxx, yyyy, zzzz, aaaa,
bbbb are all some arbitrary addresses shown
in the above figures from 6.1 to 6.4.
From the figures
6.1 to 6.4 , it is very clear that we have used only one pointer i.e
vptr , instead of four different pointers to point to four different
variable of different data
types, where space complexity
is more. Only one thing that
the programmer should keep in the mind while coding is that proper
typecasting should be done
depending on the different data types.
Void
pointers are used in places
where you need to work with different pointer types in the same code.
One commonly used
example is the library function qsort:
base
is the address of an array, nmemb
is the number of elements in the array, size
is the size of each element, and compar
is a pointer to a function that compares two elements of the array.
Pointer Arithmetic on
Void*
Let us learn how to apply pointer
arithmetic on the void pointers through the bug code as shown in the
Fig 7 given below.
Fig 7: Bug code
Fig
8: Output of the bug code shown in Fig 7
From the above result, one can
see that we are not getting the expected output. Surprisingly
what went wrong ? Let us analyze the above code & output we got.
1. From the output it is very clear
that addresses are incremented by one one byte, this is because the
gcc compiler assumes sizeof(void) is 1 byte long.
2. So, when we increment void pointer
by one, it is incremented by one byte long as one can observe this
from the Fig 8(address part).
3. Now coming to the value part, the
first value i.e arr[0] is getting printed correct, but after that all
the values are wrong, this I am explaining through the pictorial
representation as shown in the Fig 9
to Fig 13 below.
Note : The output depends on the
endianness of the architecture.
Fig 9
Fig 10
Fig 11
Fig 12
Fig 13
From the above five figures, we can see
why we are not getting the expected output. So the corrected code
along with expected output is shown in the Fig 14 & 15 given
below,
Fig 14 : Correction to the code given
in Fig 7
Fig 15: Expected output for the code
given in Fig 11.
void pointers can be assigned to any
pointer value. One cannot dereference a void pointer without proper
typecasting. Functions such as malloc, calloc, free utilize void pointers.